Private Cloud
-
- A private cloud is also known as an internal cloud or corporate cloud.
- Private cloud provides computing services to a private internal network (within the organization) and selected users instead of the general public.
- Private cloud provides a high level of security and privacy to data through firewalls and internal hosting. It also ensures that operational and sensitive data are not accessible to third-party providers.
- HP Data Centers, Microsoft, Electra-private cloud, and Ubuntu are examples of private cloud.
A private cloud is a single-tenant environment, meaning the organization using it (the tenant) does not share resources with other users. Those resources can be hosted and managed in a variety of ways. The private cloud might be based on resources and infrastructure already present in an organization’s on-premises data center or on a new, separate infrastructure, which is provided by a third-party organization. In some cases, the single-tenant environment is enabled solely using virtualization software. In any case, the private cloud and its resources are dedicated to a single user or tenant.
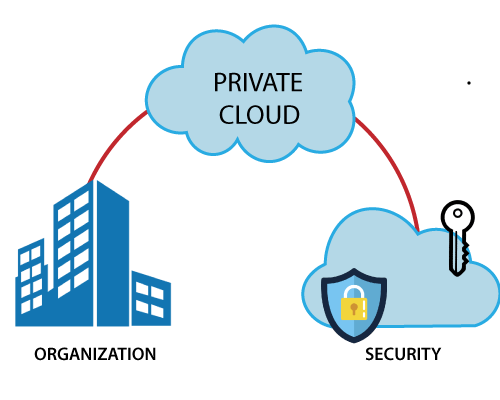
Private Cloud Cyber Security Technologies
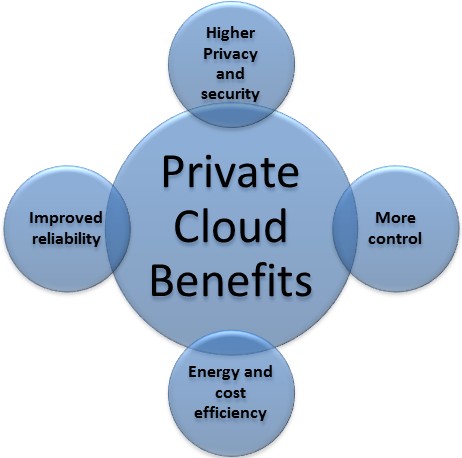
There are the following advantages of Private Cloud –
1) More Control
Private clouds have more control over their resources and hardware than public clouds because it is only accessed by selected users.
2) Security & privacy
Security & privacy are one of the big advantages of cloud computing. Private cloud improved the security level as compared to the public cloud.
3) Improved performance
Private cloud offers better performance with improved speed and space capacity.
Disadvantages of Private Cloud
1) High cost
The cost is higher than a public cloud because setting up and maintaining hardware resources are costly.
2) Restricted area of operations
As we know, the private cloud is accessible within the organization, so the area of operations is limited.
3) Limited scalability
Private clouds are scaled only within the capacity of internal hosted resources.
4) Skilled people


TECHNOLOGY
Monitors all network traffic with packet-by-packet analysis.
Patented “STEALTH” technology enables monitoring of network traffic without broadcasting an IP address.
Sized for your network’s speed and configuration

COMPLIANCE
Provides compliance with HIPPA, PCI, NIST, and SOX regulations.
Management Level Reports provide detailed analysis of hacking attempts and blocked hacks.
User portals provide extensive
EASY IMPLEMENTATON
Requires NO changes to your network topology or configuation.
Automated Artificial Intelligence functions manage security policies and track trends


