Public Cloud
- Public Cloud provides a shared platform that is accessible to the general public through an Internet connection.
- Public cloud operated on the pay-as-per-use model and administrated by the third party, i.e., Cloud service provider.
- In the Public cloud, the same storage is being used by multiple users at the same time.
- Public cloud is owned, managed, and operated by businesses, universities, government organizations, or a combination of them.
- Amazon Elastic Compute Cloud (EC2), Microsoft Azure, IBM’s Blue Cloud, Sun Cloud, and Google Cloud are examples of the public cloud.
Public Cyber Security Technologies at Work For You
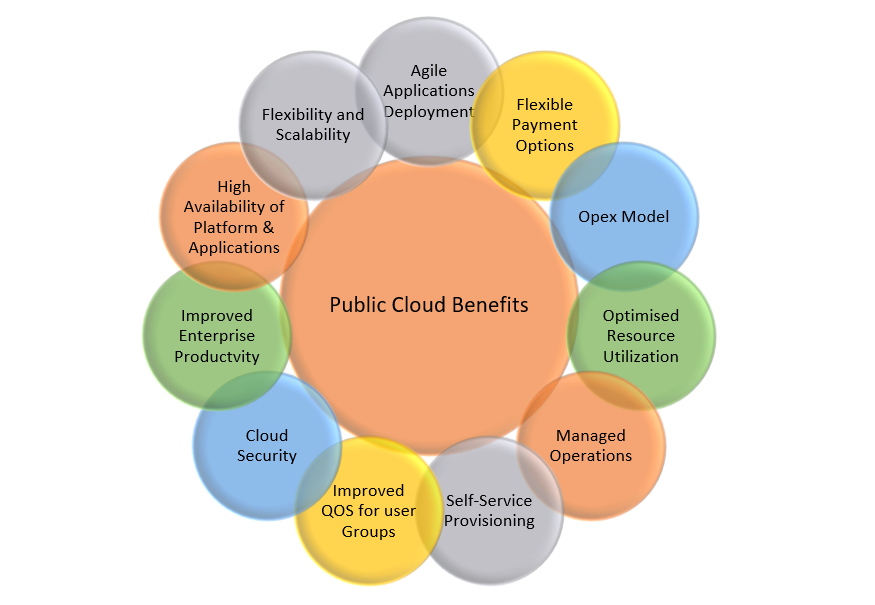
Advantages of Public Cloud
There are the following advantages of public cloud –
1) Low Cost :Public cloud has a lower cost than private, or hybrid cloud, as it shares the same resources with a large number of consumers.
2) Location Independent :Public cloud is location independent because its services are offered through the internet.
3) Save Time :In Public cloud, the cloud service provider is responsible for the manage and maintain data centers in which data is stored, so the cloud user can save their time to establish connectivity, deploying new products, release product updates, configure, and assemble servers.
4) Quickly and easily set up :Organizations can easily buy public cloud on the internet and deployed and configured it remotely through the cloud service provider within a few hours.
5) Business Agility :Public cloud provides an ability to elastically re-size computer resources based on the organization’s requirements.
6) Scalability and reliability :Public cloud offers scalable (easy to add and remove) and reliable (24*7 available) services to the users at an affordable cost
Disadvantages of Public Cloud
1) Low Security :Public Cloud is less secure because resources are shared publicly.
2) Performance :In the public cloud, performance depends upon the speed of internet connectivity.
3) Less customizable :Public cloud is less customizable than the private cloud.

TECHNOLOGY
Monitors all network traffic with packet-by-packet analysis.
Patented “STEALTH” technology enables monitoring of network traffic without broadcasting an IP address.
Sized for your network’s speed and configuration

COMPLIANCE
Provides compliance with HIPPA, PCI, NIST, and SOX regulations.
Management Level Reports provide detailed analysis of hacking attempts and blocked hacks.
User portals provide extensive
EASY IMPLEMENTATON
Requires NO changes to your network topology or configuation.
Automated Artificial Intelligence functions manage security policies and track trends


